|
LET’S INTRODUCE what’s new Get familiar with the new concepts introduced by Workload Automation on Cloud that leverage the 9.5 Fix Pack 1 on-premise version, released in July:
Before we get into explaining how to delegate administrative tasks to other users in your subscription, let’s first start with:
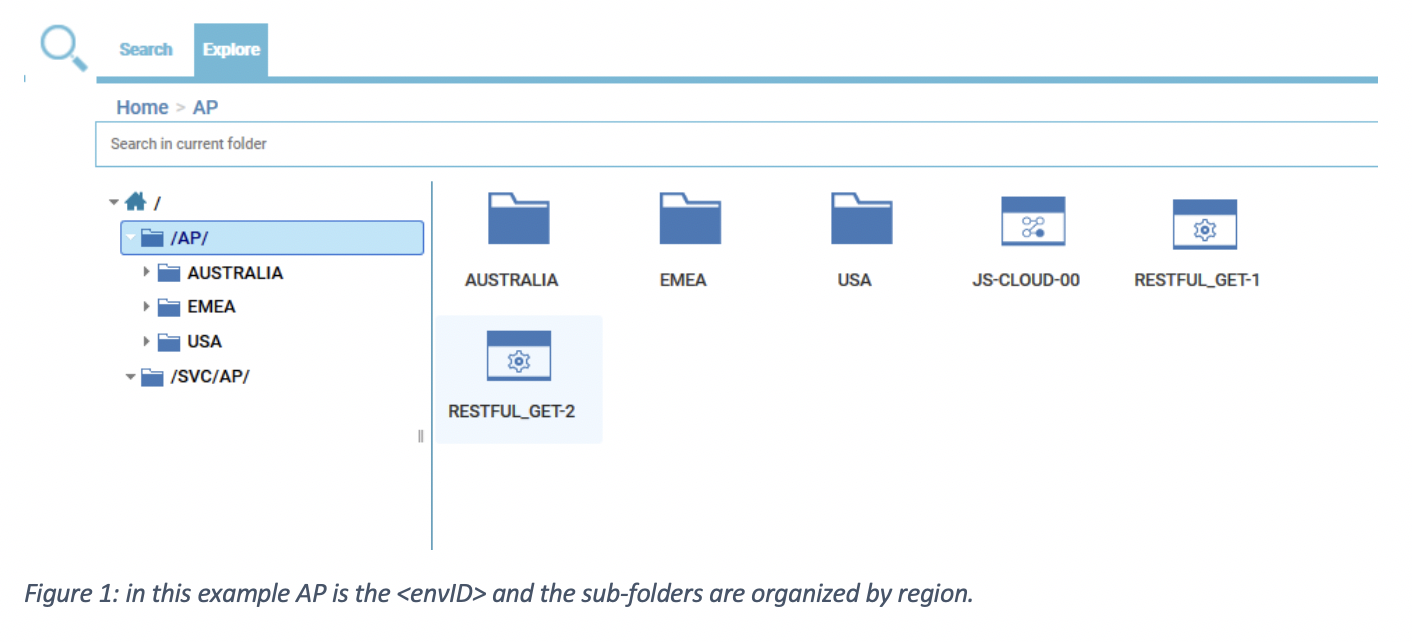
Explore the subscription folder A folder named /<envID> (e.g. /AP) is automatically created when the subscription is generated. The subscription owner (for example, the user that creates the subscription) is authorized to administrate only this folder and its subfolders. When the owner uses the Workload Designer in the Dynamic Workload Console to define scheduling objects, the Explorer view automatically displays the <envID> folder and its contents. Another folder the user can see is /SVC/<envID>: this is a read-only service folder used to manage job streams that enable services from the Self-Service Catalog. What kind of workstation can the subscription owner manage? A subscription owner can work with the following workstations:
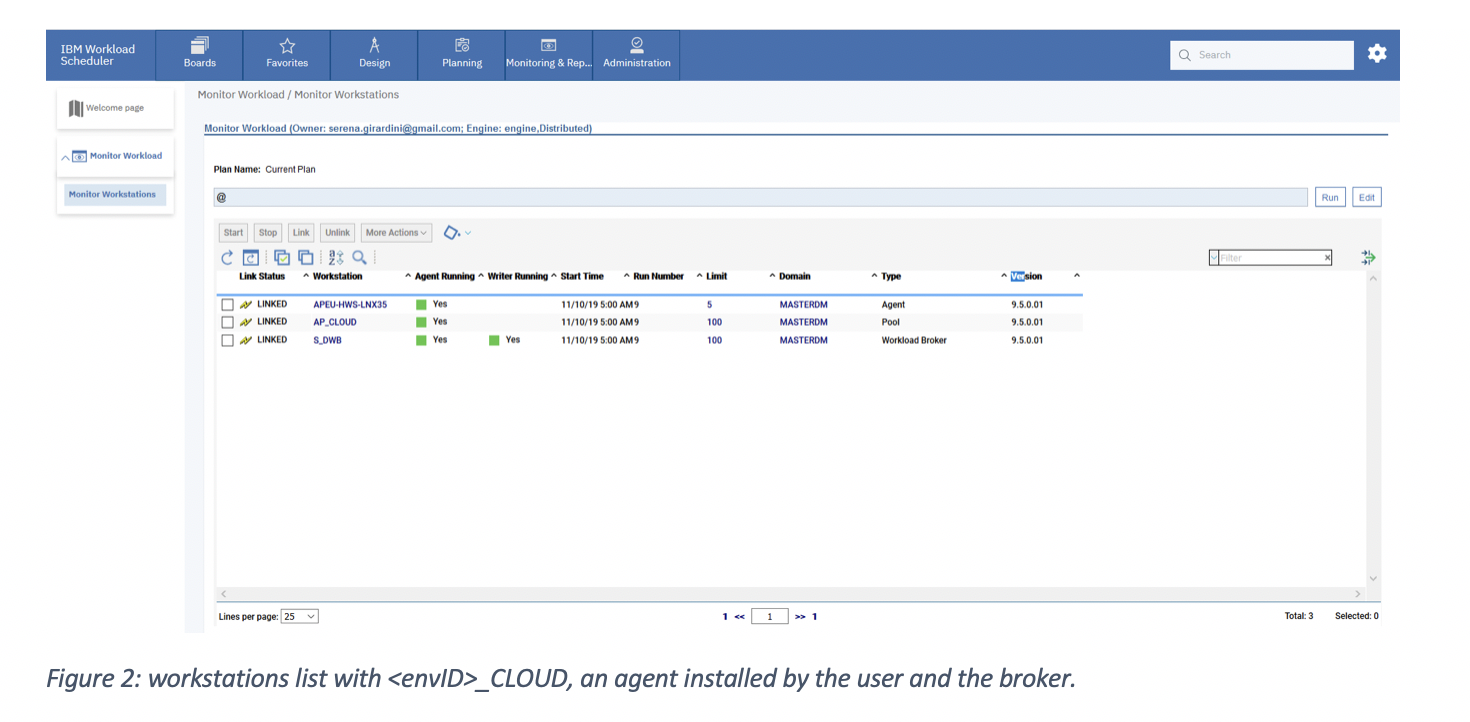
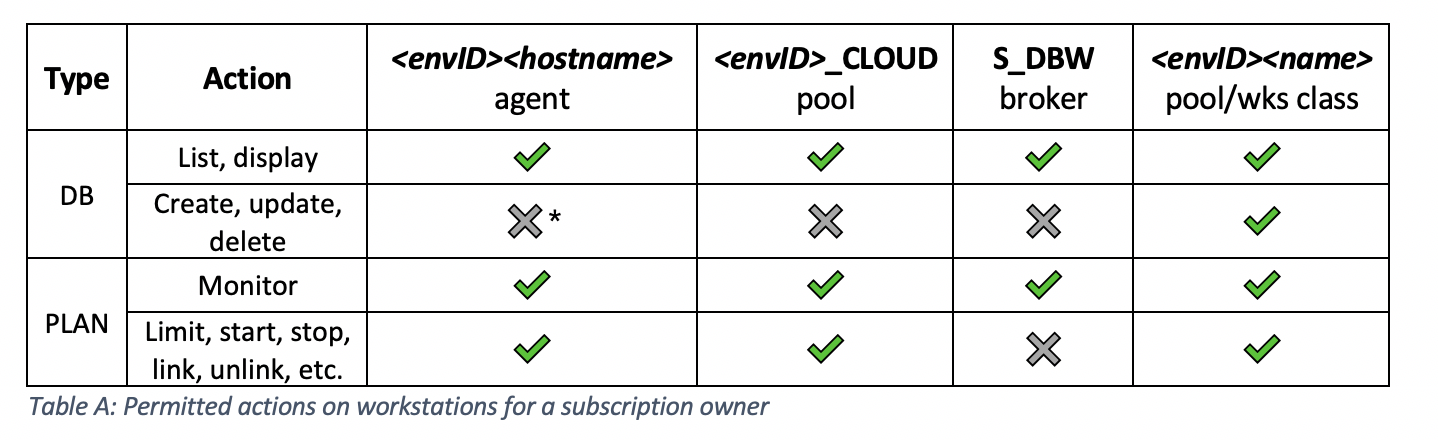
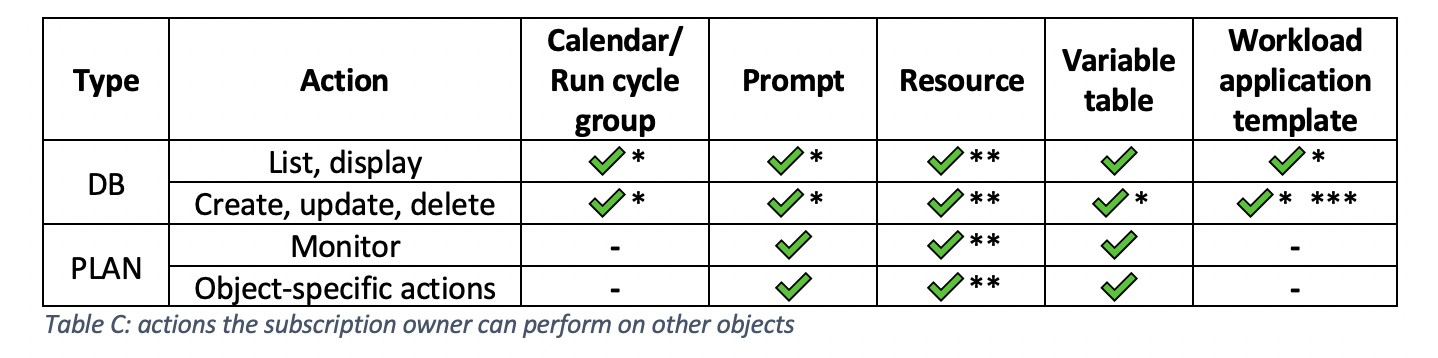
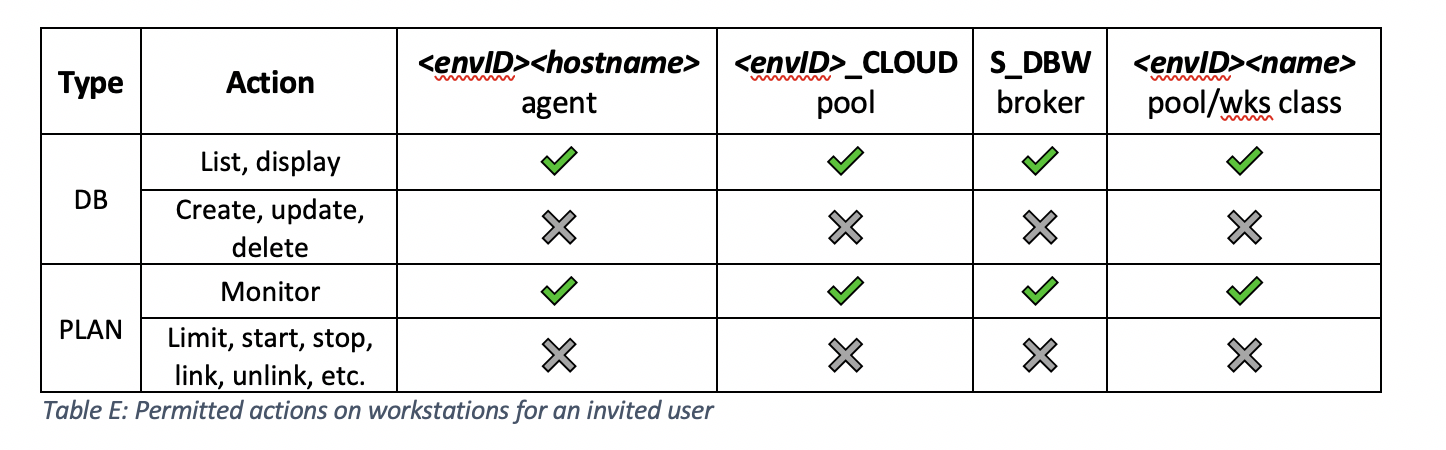
Let’s explore the possible actions the subscription owner can perform on these workstations: * agents cannot be added because they automatically register when they are installed. What actions can a subscription owner perform on scheduling objects?
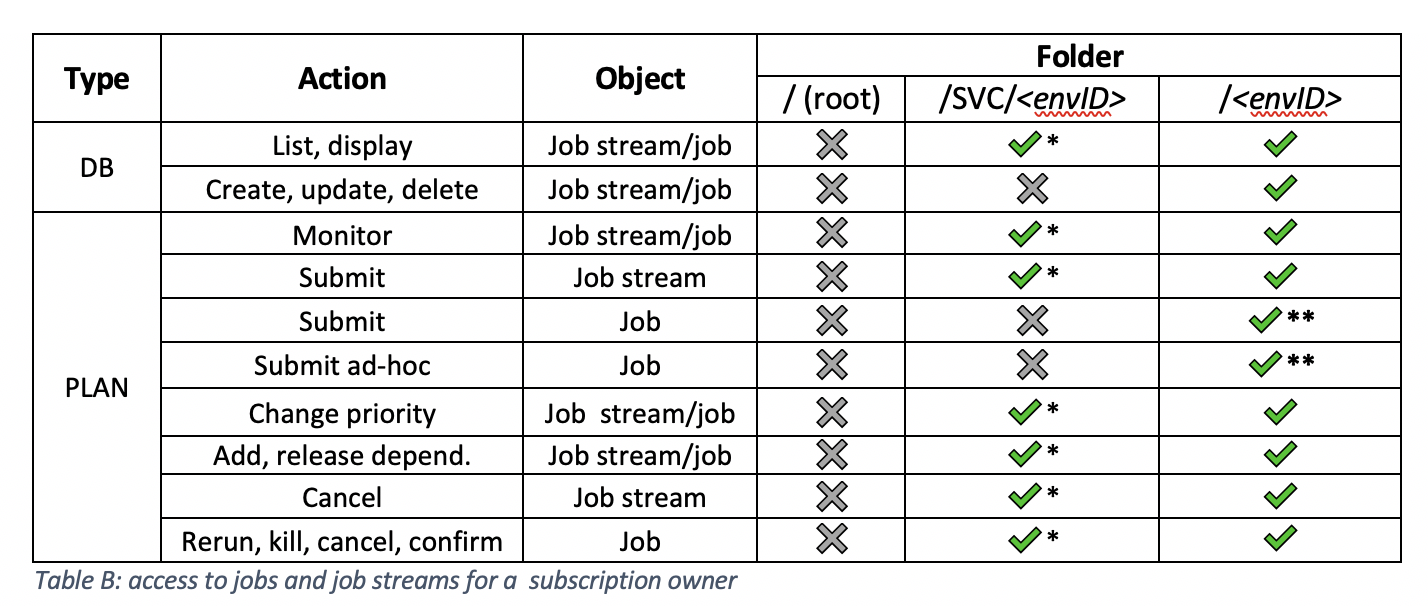
* In the /SVC/<envID> folder, the user is authorized to manage only job streams and jobs related to the Self-Service Catalog service requests. ** NOT authorized on <envID>_CLOUD pool workstation. The subscription owner is not able to submit predefined jobs or submit ad hoc jobs in the /JOBS job stream, but an owner can submit into a predefined job stream that is already submitted into the PLAN.
* object name must start with the <envID> prefix, otherwise, the subscription user is not authorized to save it. ** also on the S_DWB broker workstation. *** workload application templates can contain only objects that the user can manage (for example, it cannot contain job streams defined in /SVC/<envID> folder).
Event Provider:
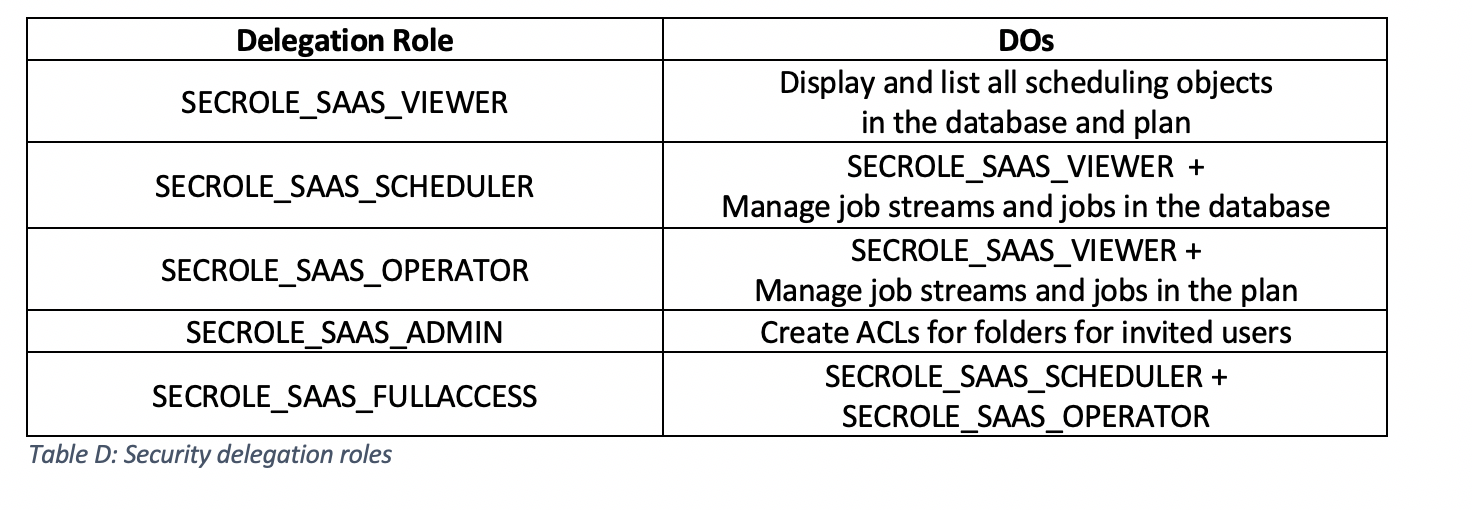
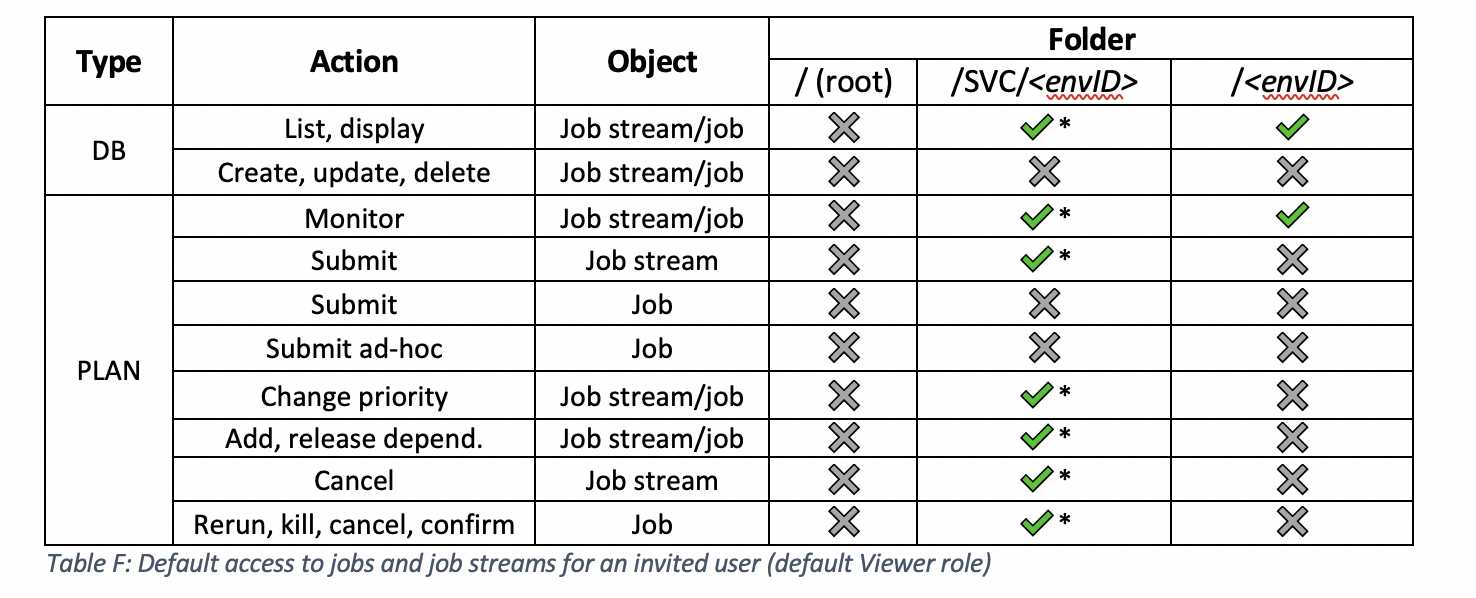
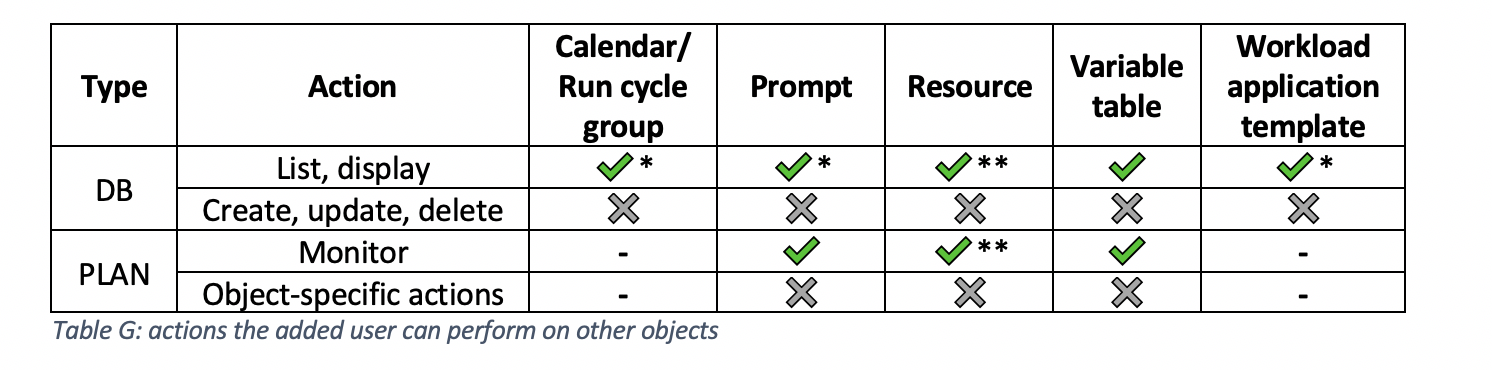
What are the available roles for delegation in the subscription folder or subfolders? Users invited to an existing subscription are created with limited privileges. The subscription owner can create access control lists (ACL) for users in its subscription giving them accesses to jobs and job streams in specific folders. You can delegate administrative privileges only for operating on jobs and job streams. To grant privileges on other object types, contact customer support. Each ACL can grant access to jobs and job streams in the parent folder (<envID> folder) and the user can manage the entire folder hierarchy. If instead access is granted on a subfolder of the parent folder, the user can manage jobs and job streams in this subfolder and any of its child folders. The following table shows the security roles that can be assigned to a user: Subscription owner vs Invited user Compared with an invited user, the subscription owner can access a larger set of objects. By default, a new user is added to Workload Automation on Cloud with the SECROLE_SAAS_VIEWER role assigned, which means that the user can only display and list scheduling objects. The following tables show actions that an invited user can perform by default. As we explained earlier, the subscription owner can assign different roles to the user to augment privileges only on job and job streams.
* the only job streams and jobs you can access in the /SVC/<envID> folder are the ones related to Self-Service Catalog service requests. ** NOT authorized on <envID>_CLOUD pool workstation.
* object name must start with the <envID> prefix, otherwise the subscription user is not authorized to save it. ** also on the S_DWB broker workstation. *** workload application templates can contain only objects that a user can manage (e.g. it cannot contain job streams defined in the /SVC/<envID> folder). LET’S BEGIN delegating administrative tasks The subscription owner performs the following steps to delegate administrative privileges to other users:
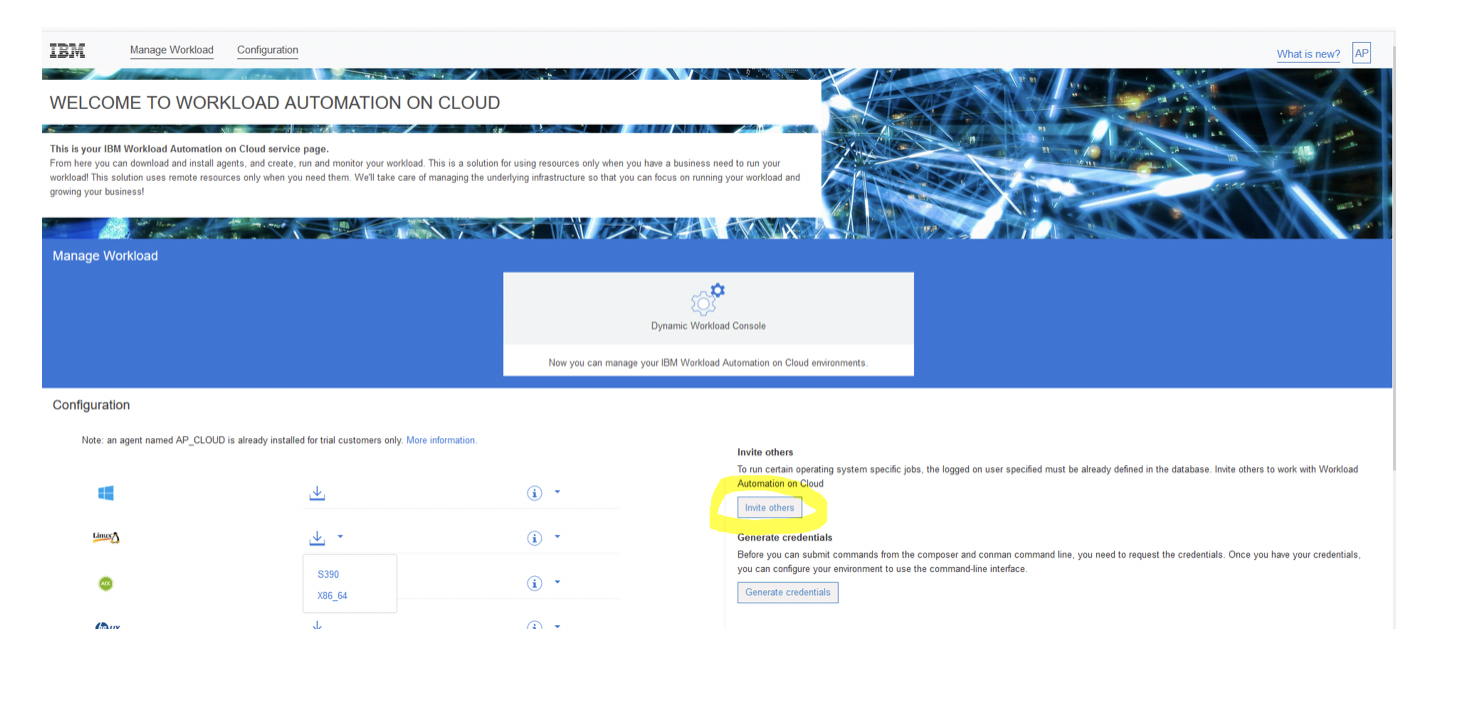
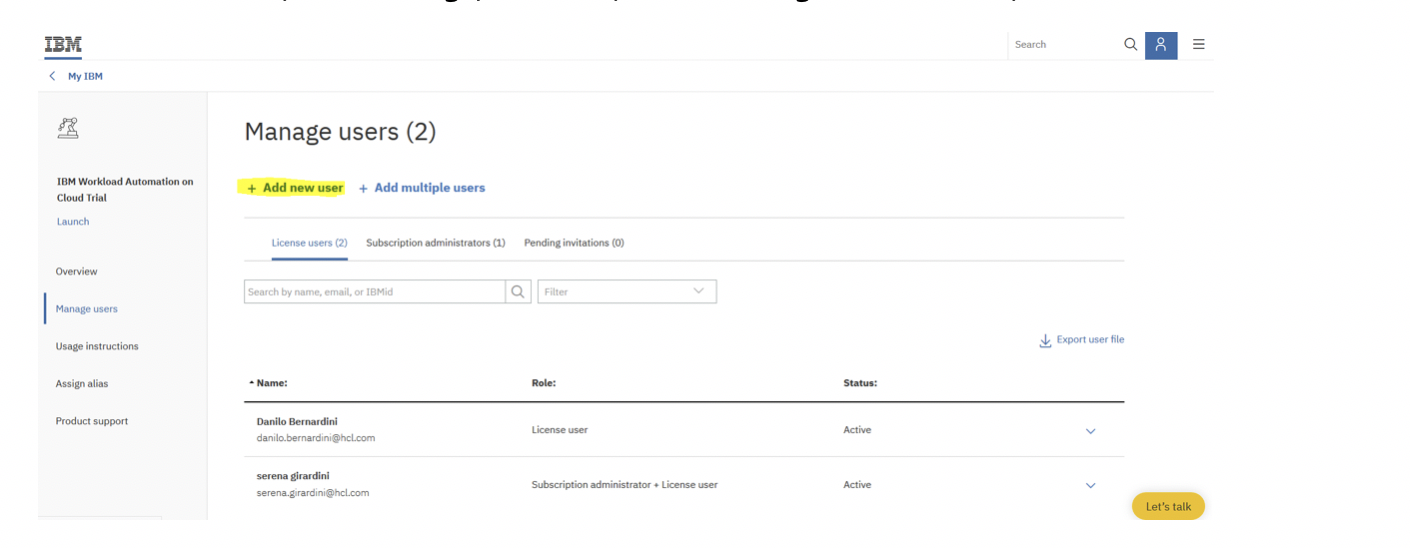
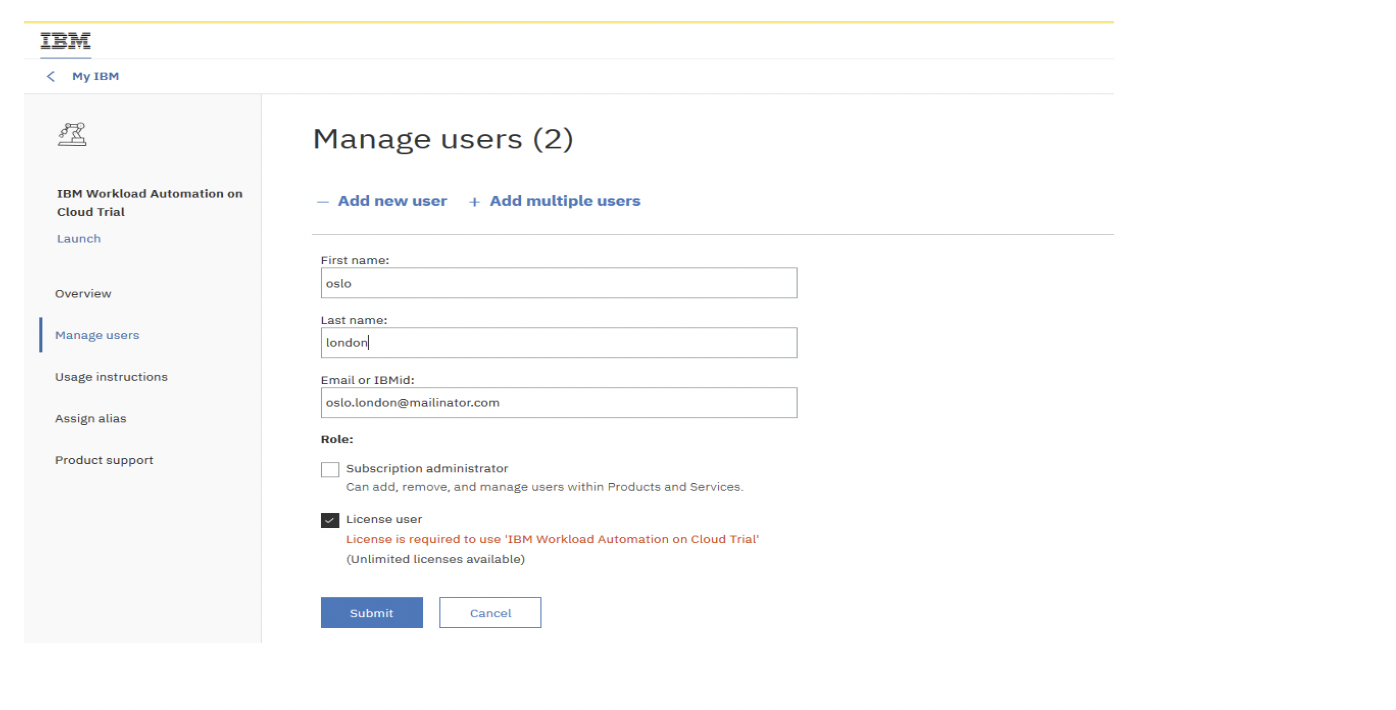
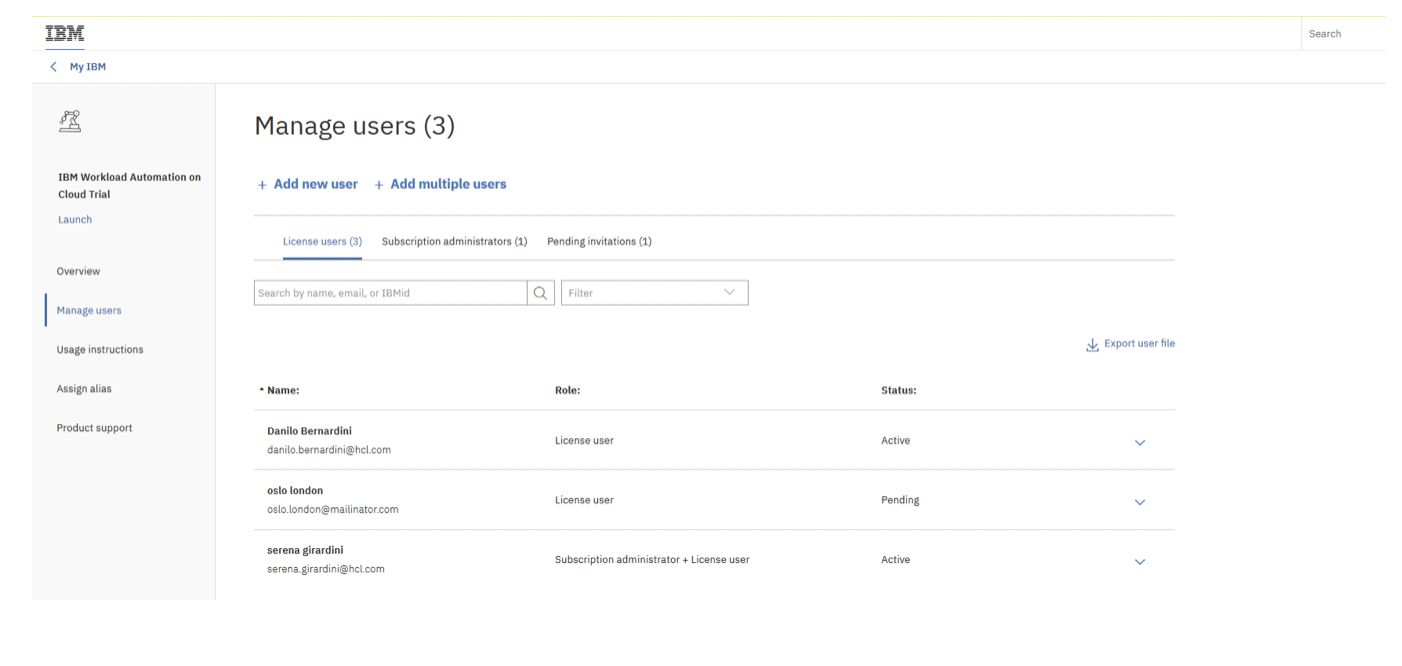
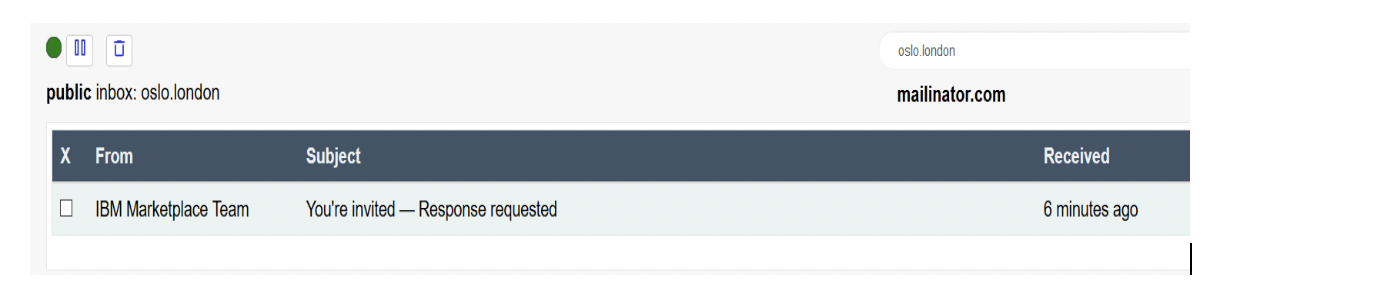
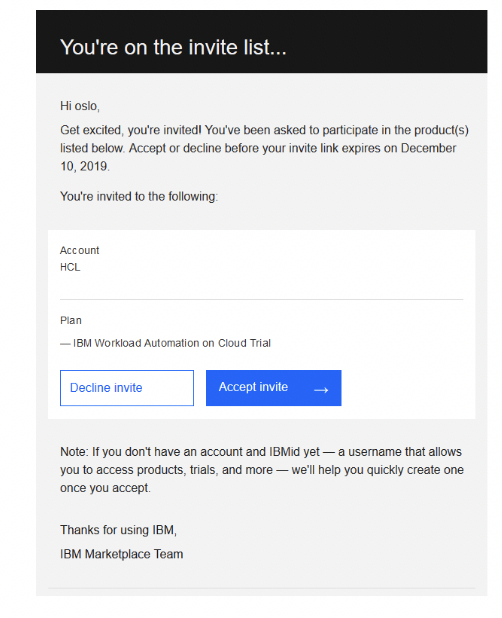
To add a new user, click Manage, and then, in the Manage users section, click Add new user: Add the user to your subscription. In this example, the user [email protected] is added. Click Submit to display the following result: The status remains Pending until the [email protected] user accepts the subscription invite in his email account. The status then becomes Active. The [email protected] user finds the following email from the IBM Marketplace team: The invited user must open the email and click Accept invite and follow the instructions. A mailinator account cannot be used in the production environment. It is used here as an example in a preproduction environment.
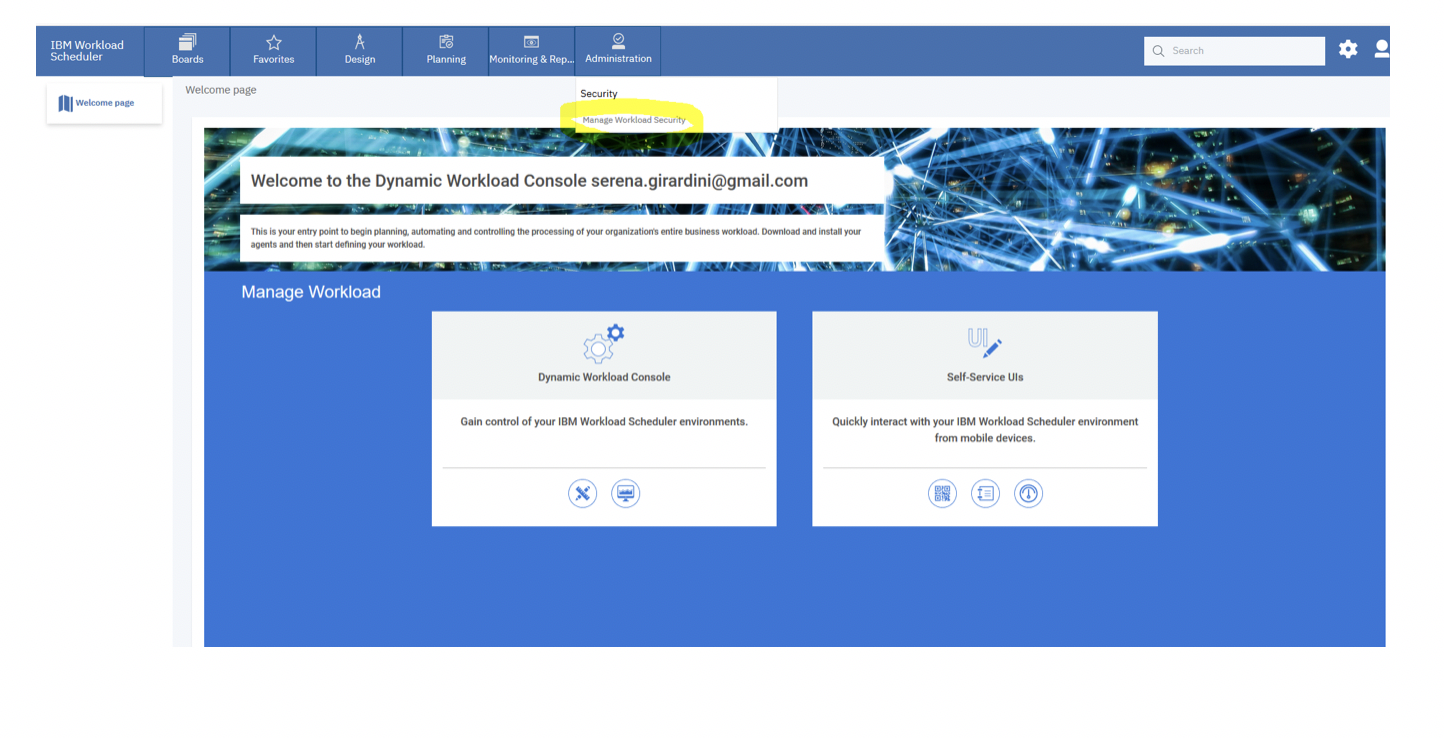
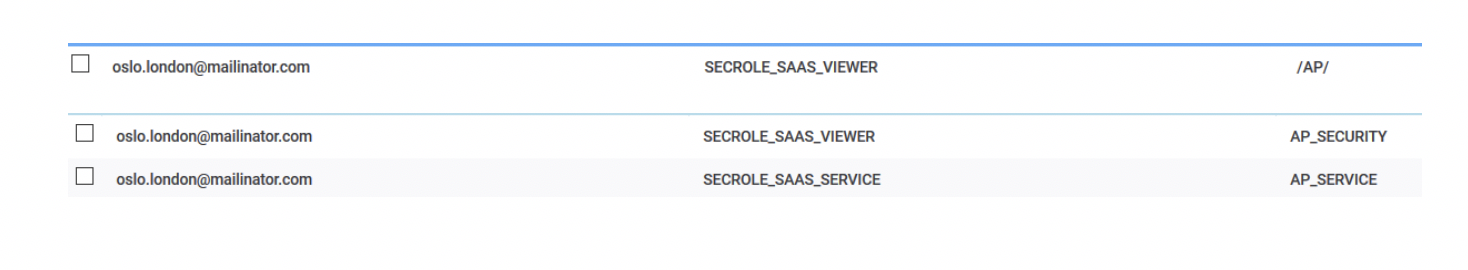
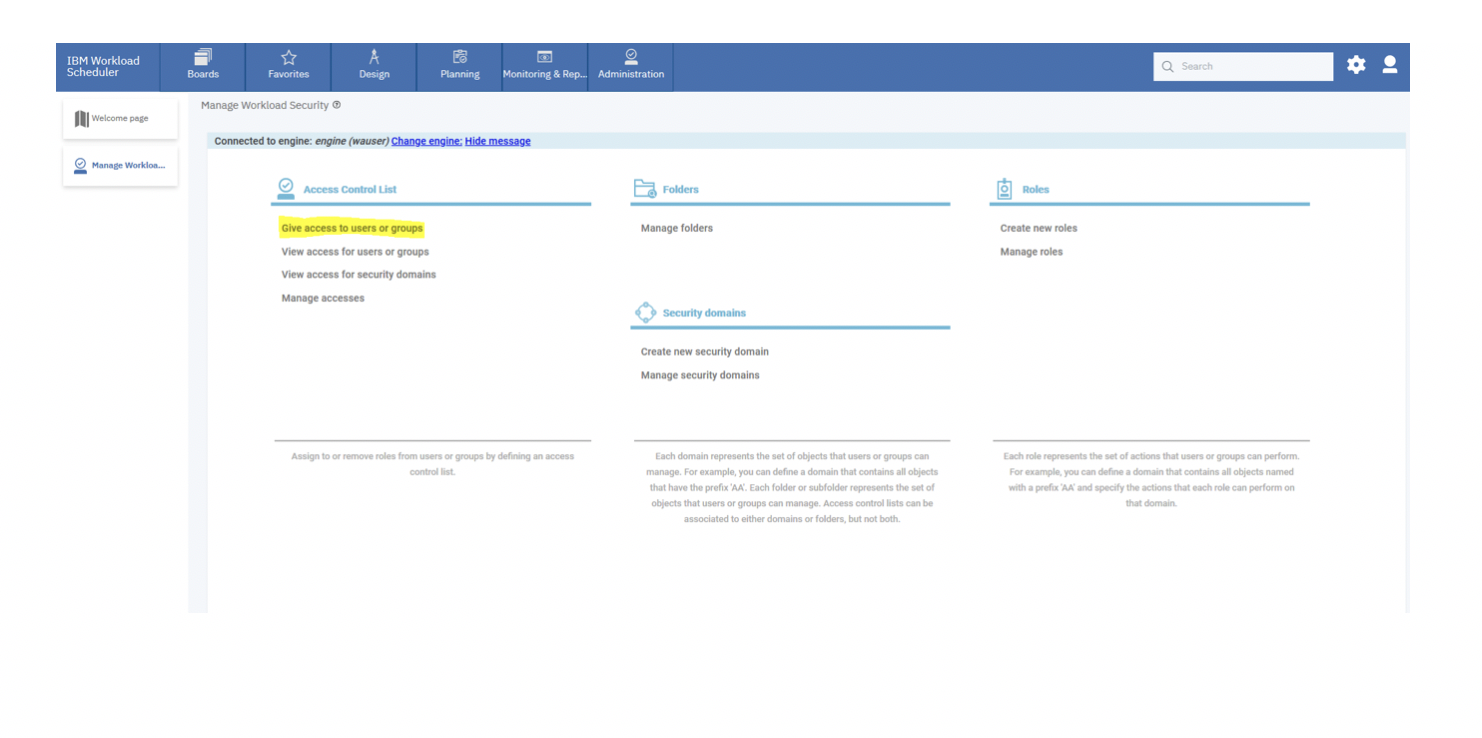
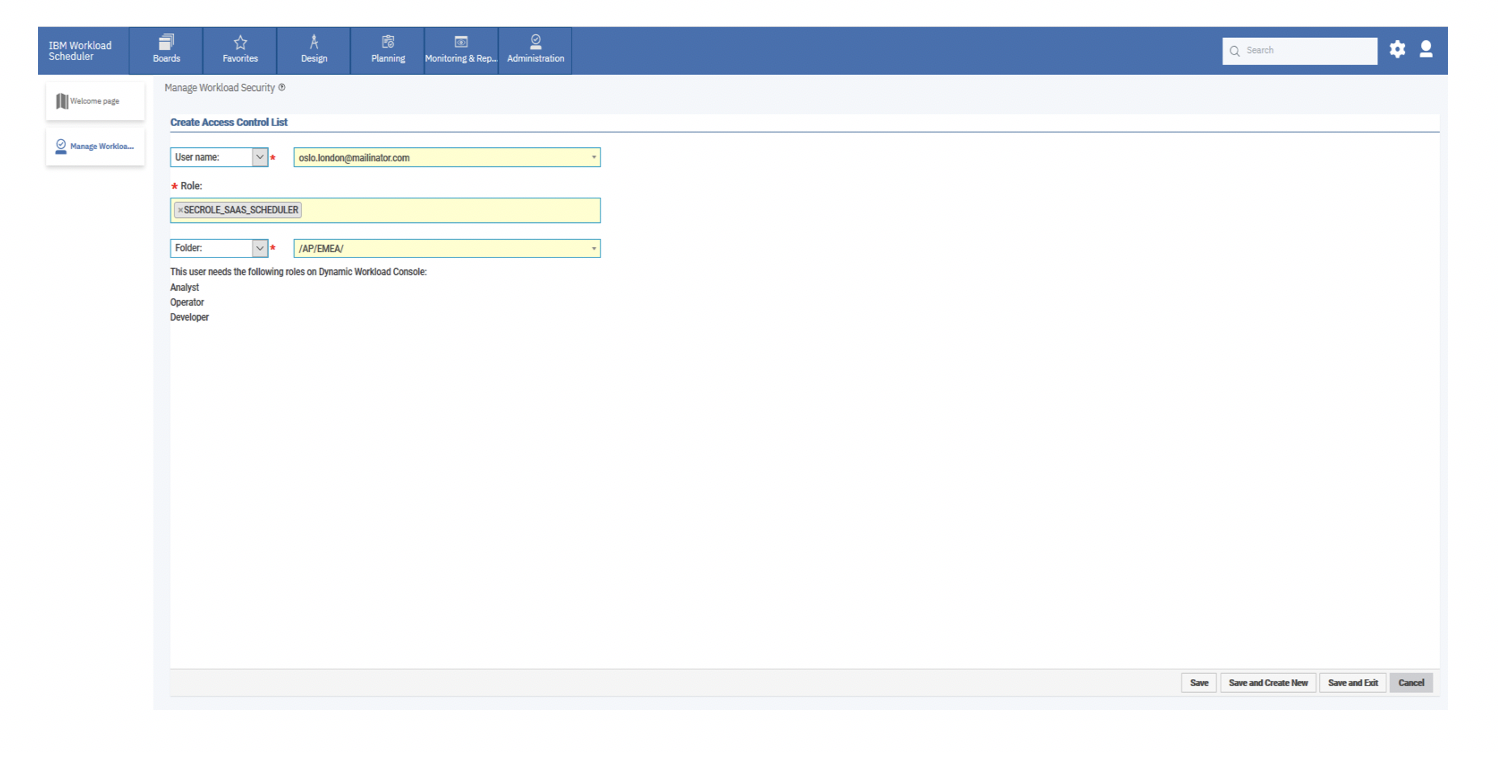
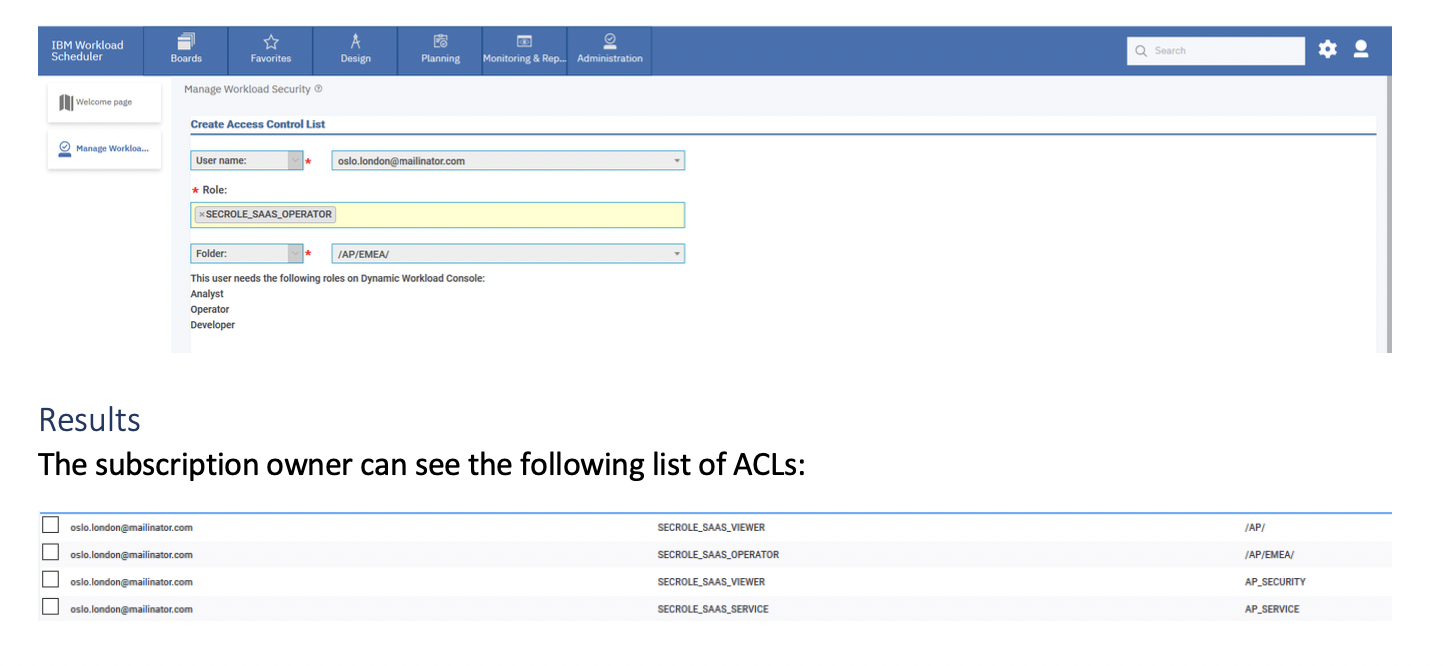
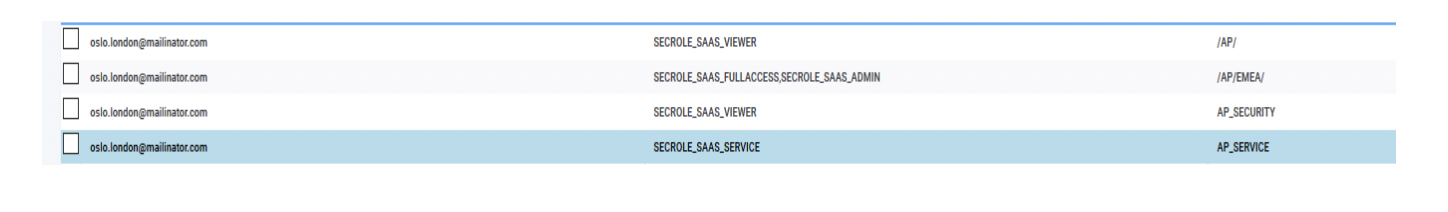
From the Manage Workload Security page, the subscription owner can click on Manage Access in the Access Control List (ACL) section, and see that the user [email protected] has the following ACL setting on the /AP/ folder and in the AP_SECURITY and AP_SERVICE domains: From the Manage Workload Security page, to grant a user rights on the <envID> folder and its sub folders, the subscription owner can click on Give access to users or groups from the Access Control List (ACL) section. 2a) Delegate SECROLE_SAAS_SCHEDULER role to the user: Procedure:On the Create Access Control List page, do the following:
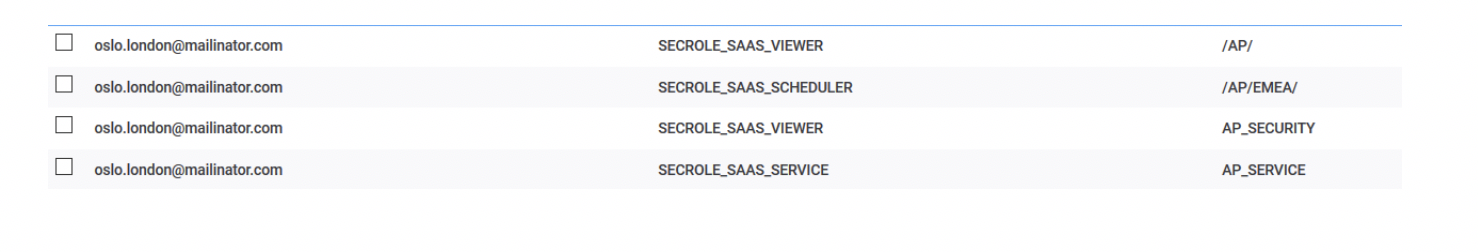
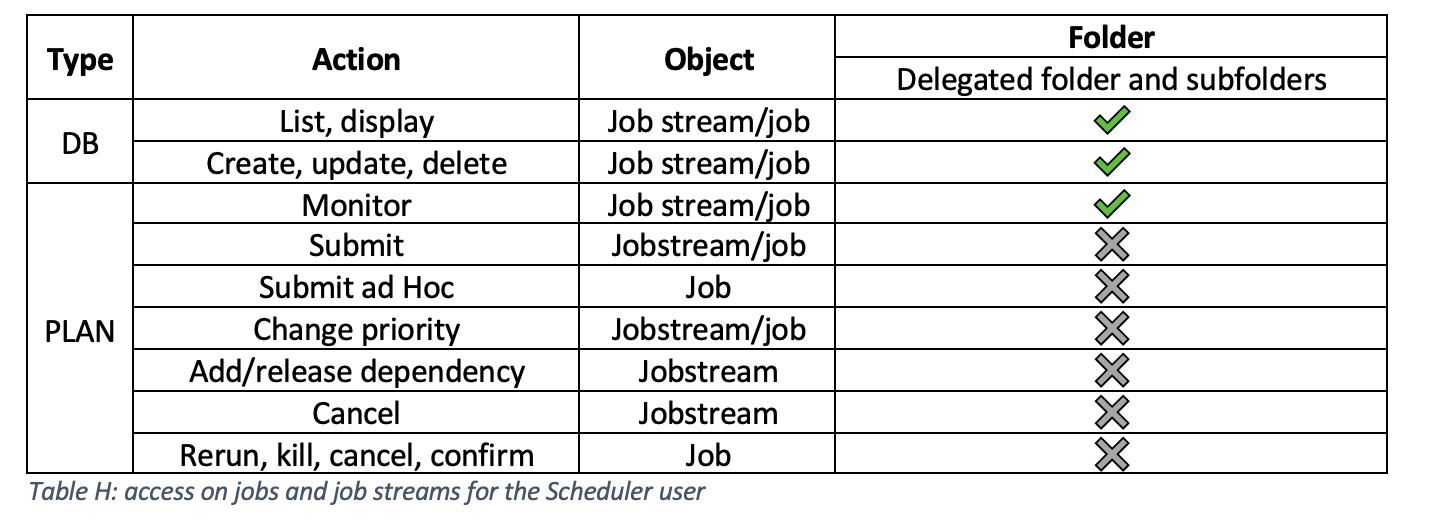
ResultsFrom the list of ACLs, the subscription owner can see the following list: The following table shows the actions that the Scheduler user can now perform on jobs and job streams in the delegated folder (and all its subfolders): SECROLE_SAAS_SCHEDULER is not able to submit newly created job streams or jobs, so users with this role need to ask the subscription owner or a user that has either the SECROLE_SAAS_OPERATOR or SECROLE_SAAS_FULLACCESS role on the same folder to submit these job streams and jobs. SECROLE_SAAS_SCHEDULER is not able to define and manage event rules. SECROLE_SAAS_SCHEDULER is not able to define calendars, run cycles, prompts, resources, workload application templates, variable tables, etc, but users with this role can use them in existing job stream definitions (if already created by the subscription owner). 2b) Delegate SECROLE_SAAS_OPERATOR role: Procedure:On the Create Access Control List page, do the following:
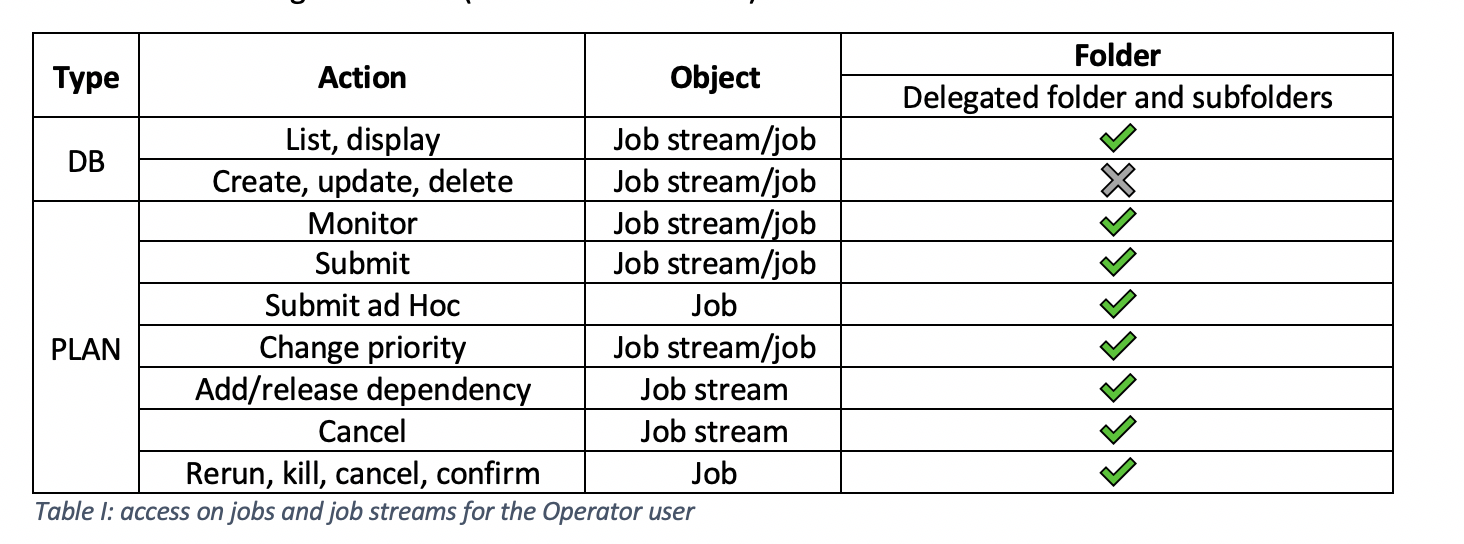
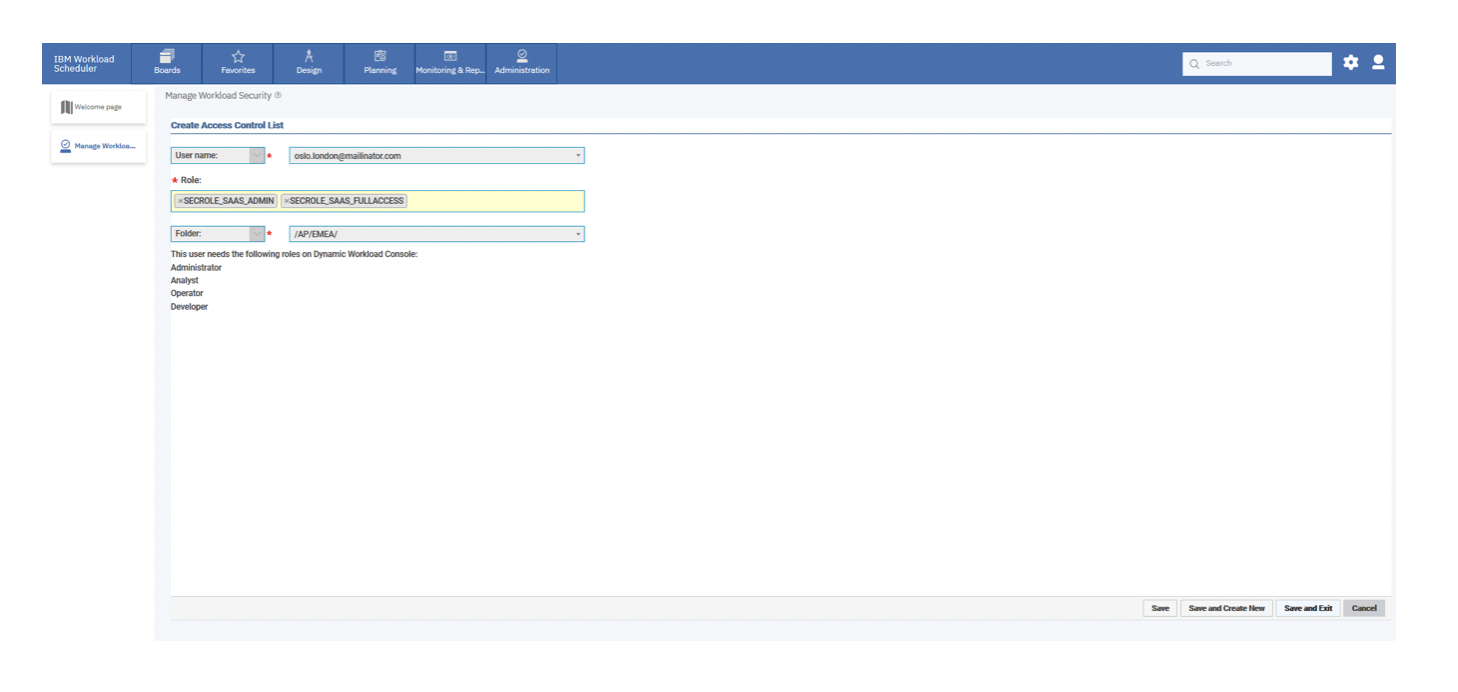
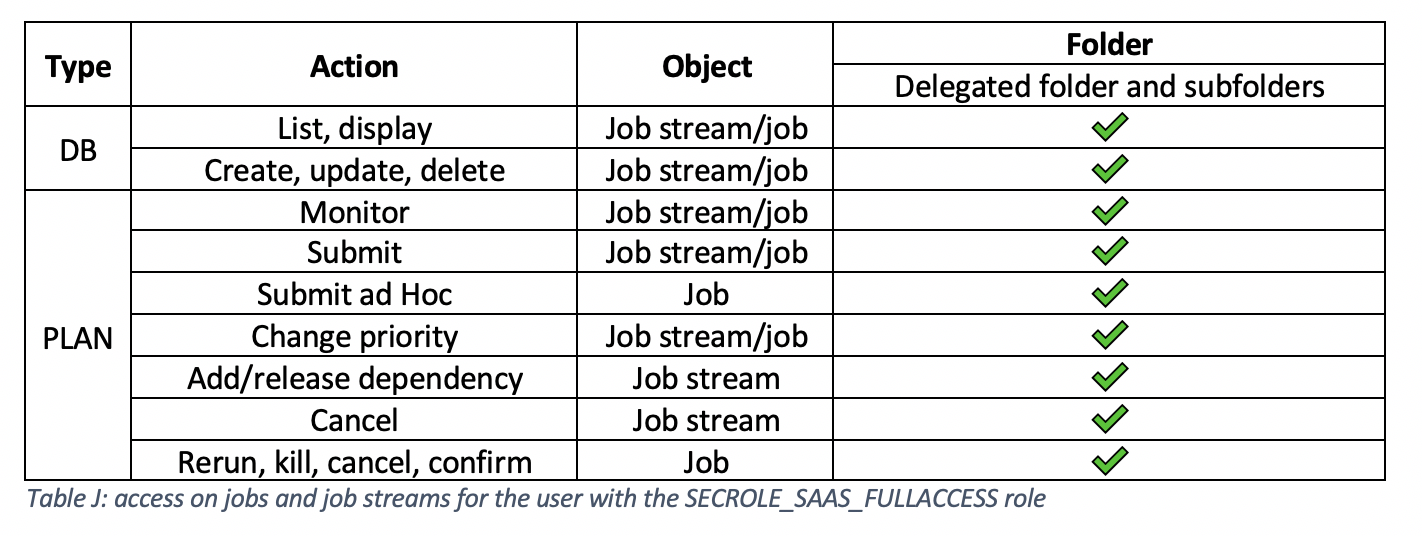
The following table shows the actions that the Operator user can now perform on jobs and job streams in the delegated folder (and all its subfolders): 2c) Delegate SECROLE_SAAS_FULLACCESS and SECROLE_SAAS_ADMIN role: Procedure:On the Create Access Control List page, do the following:
ResultsThe subscription owner can see the following list of ACLs: The following table shows the actions that the user with the SECROLE_SAAS_FULLACCESS role can now perform on jobs and job streams in the delegated folder (and all its subfolders): SECROLE_SAAS_ADMIN role allows [email protected] to define ACLs on the delegated folder, in our example, /AP/EMEA and its subfolders. After the owner delegates [email protected] to have the SECROLE_SAAS_ADMIN andSECROLE_SAAS_FULLACCESS roles, [email protected] has full administrative privileges on the subscription only for jobs and job streams, but not for the other scheduling objects. LET’S THINK about the future: The delegation of the administrative tasks to other users in the subscription is currently limited to jobs and job streams. This limitation remains until a subsequent update of Workload Automation on Cloud is rolled out, where the folder concept is extended to the other scheduling objects.
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
July 2024
Categories
All
|





 RSS Feed
RSS Feed