|
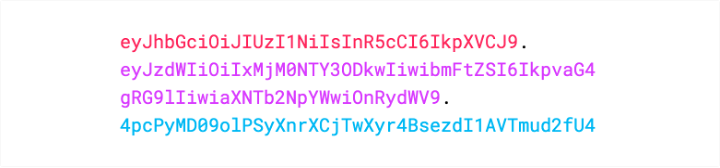
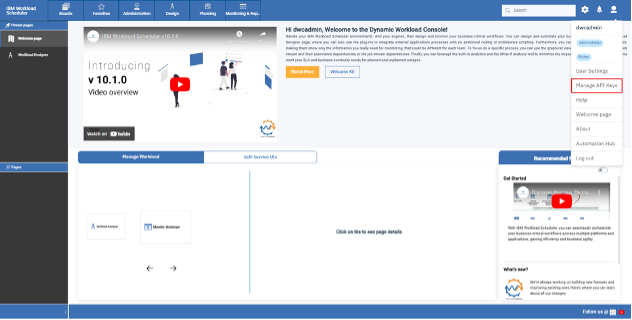
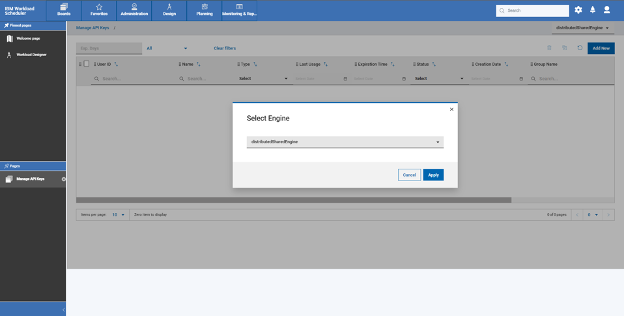
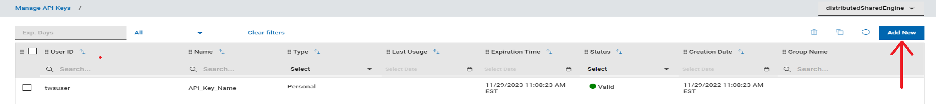
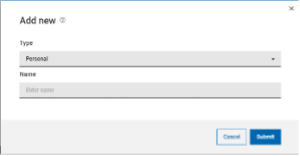
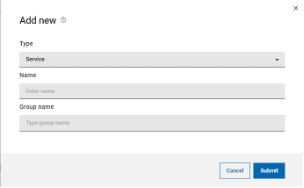
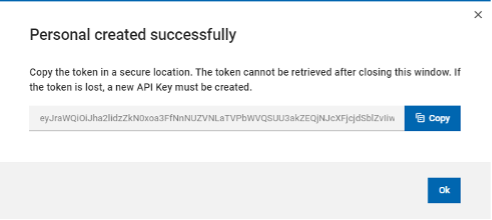
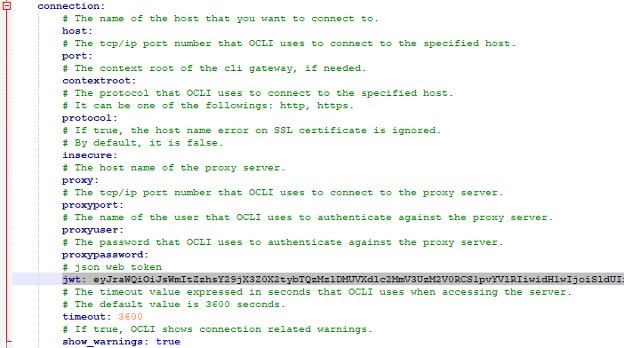
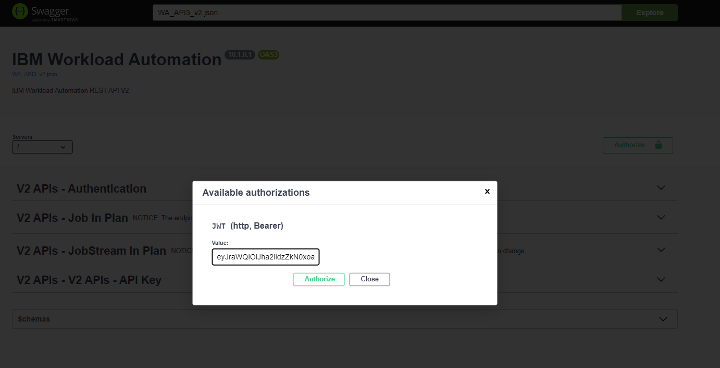
JSON Web Token (JWT) is an open standard (RFC7519) which describes a compact and easy-to-use structure to securely connect two parties in a public or private network through a JSON object. The token can be digitally signed, for example through a public and private key pair (e.g. RSA). A signed JWT token contains a series of claims. The integrity of these claims can be verified, authorizing the owner of the token to access to APIs, services, and resources declared on the claims. The compact nature of the JWT is due to its unique structure, which is composed of three encoded components (Header, Payload - where the claims are declared - and Signature) separated by a dot character (.), as follows: The JWT can be sent in an HTTP request - for example as an HTTP parameter or POST parameter - in every action that requires the user to be authorized: exploited in such a mechanism, the JWT is a secure, lightweight and user-friendly alternative to basic authentication on the web. Starting from version 10.1 Fix Pack 1, Workload Automation enables you to create a JWT and use it to access its resources through the API Key. Let's dive in and see how! API Key creation To use the JWT, you have to create an API Key. Login into the Dynamic Workload console, select the User menu and then select Manage API Keys. Select an engine from the engine list and click apply. Click “Add New” Now, you can create either a Personal or a Service API Key. A Personal API Key identifies a real user executing operations on Workload Automation, whereas a Service API Key is a special kind of key which identifies an account that is not associated to a real user. Click Submit and copy the JWT token to use it. JWT Usage After you have created the JWT token and stored it in a secure place, you can provide it as input to authorize API calls. The token can be used through the Orchestration CLI or the Swagger UI. To authorize actions on the Orchestration CLI, you must add the JWT token in the connection section in the configuration file, named “config.yaml”, located in the “$HOME/.OCLI” folder. To authorize actions on the Swagger UI, you must click Authorize and add the JWT token as value in the Available authorizations dialog. Click Authorize and start performing any secure API call. JWT: why should I use it? Using the new API Keys in Workload Automation is extremely useful and intuitive: its usage grants you a series of advantages ranging from security to user experience. First, the JWT is stored at the client level only: each JWT is digitally signed, so an attacker cannot tamper with it. Moreover, it is kept nowhere in your engine installation, and it cannot be exposed if whoever is using it keeps it safe. This also implies that there is no need to look it up on the server to verify it, so it grants access to Workload Automation resources in a quick and efficient way. Using JWT is made even much easier thanks to the implementation of the API Keys, through which the user can easily create new JWT tokens or revoke the old ones. All you need to do is create your token, store it somewhere on your machine, and then use it whenever you want to authenticate on your Workload Automation environment: all your resources are just a few clicks away! Authors Bio
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
July 2024
Categories
All
|





 RSS Feed
RSS Feed