|
Workload Scheduler allows now to protect not only its resources like Applications, Special resources, Jobs or all the objects present in the Current Plan or in the Database, but also actions and commands. For example, the Workload Scheduler execution information are stored in a VSAM file called Current Plan. The execution workflows are defined through Applications including Operations (jobs), Dependencies and other resources. Currently an WSz user can either have READ or UPDATE access to the Current plan. A user with UPDATE access can add new workload, edit occurrences, restart jobs, hold, nop, un-nop, release jobs and many other actions and commands. With the enhancement provided in the Security feature it is possible to address to implement different access levels (actions, commands) based on the User role. So now you can easily address scenarios like the following: Allow the System Administrator to:
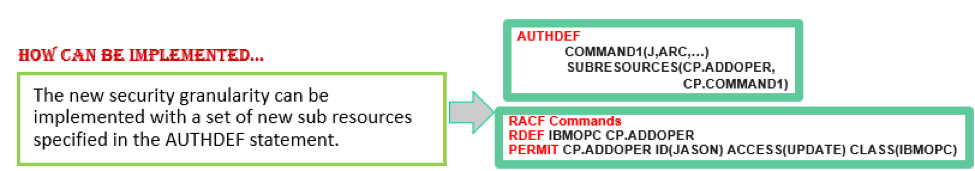
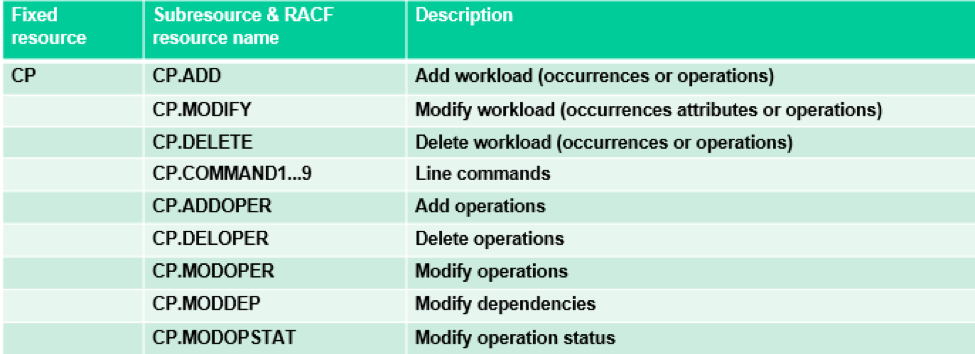
How to implement? The old instrument of AUTHDEF parameter with its SUBRESOURCES has been extended with the addition of new subresources. So the implementation steps are still two: For example, if you have RACF as SAF product: Using the new subresources you can implement scenarios like those described above. The previous example shows how you can create more User Profiles that group several commands so that a number of users, with similar profiles, can be associated to a certain COMMANDx. The new subresources, available to authorize specific command actions on the CP occurrences and operations, are the following: …and the commands that can be grouped in each COMMANDx subresource are the following: Note that both Occurrence and Operation commands can be specified in the same COMMANDx parameter.
2 Comments
Sreenath
9/26/2017 05:43:14 am
Hi Raffaella,
Reply
raffaella viola
9/26/2017 10:36:56 am
Hello,
Reply
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
July 2024
Categories
All
|







 RSS Feed
RSS Feed