|
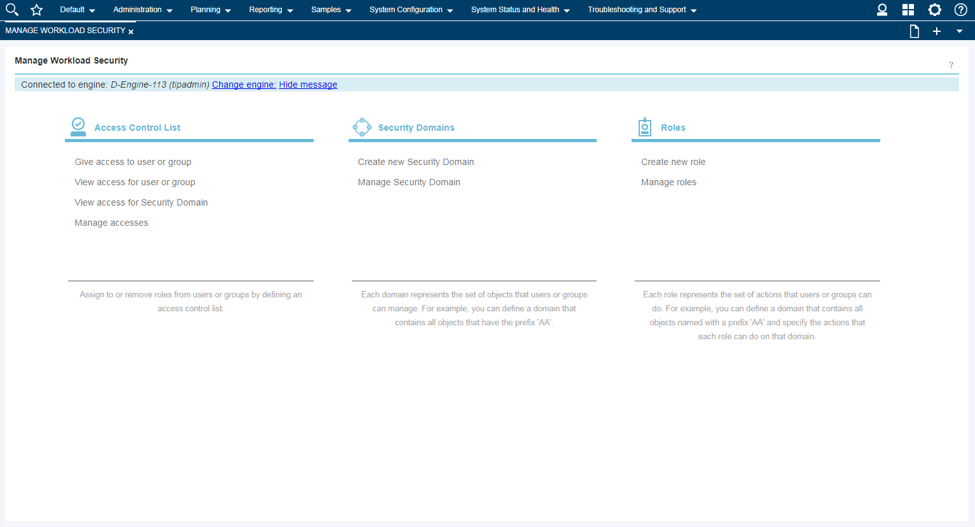
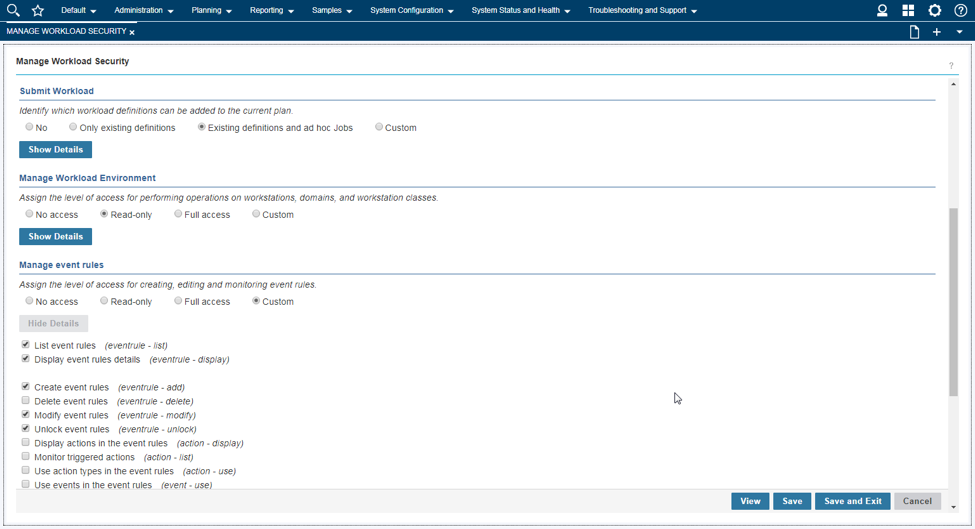
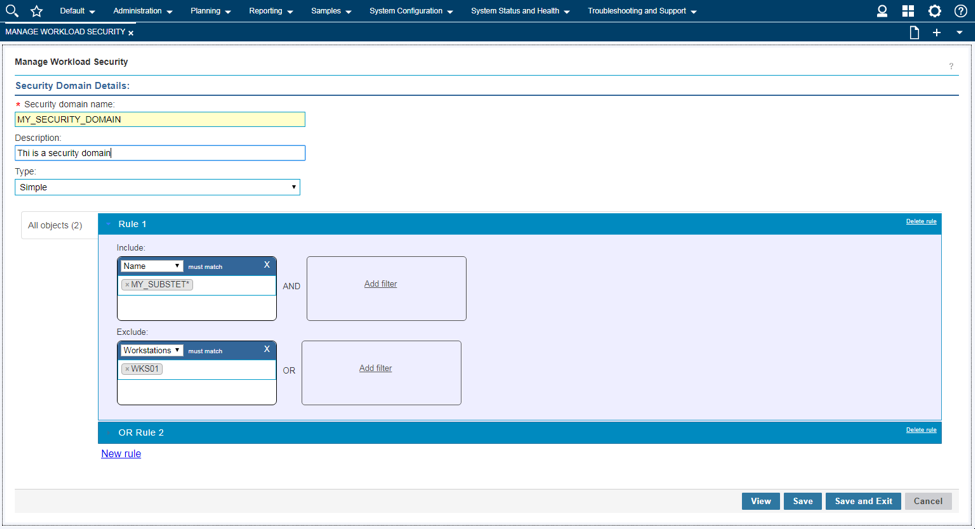
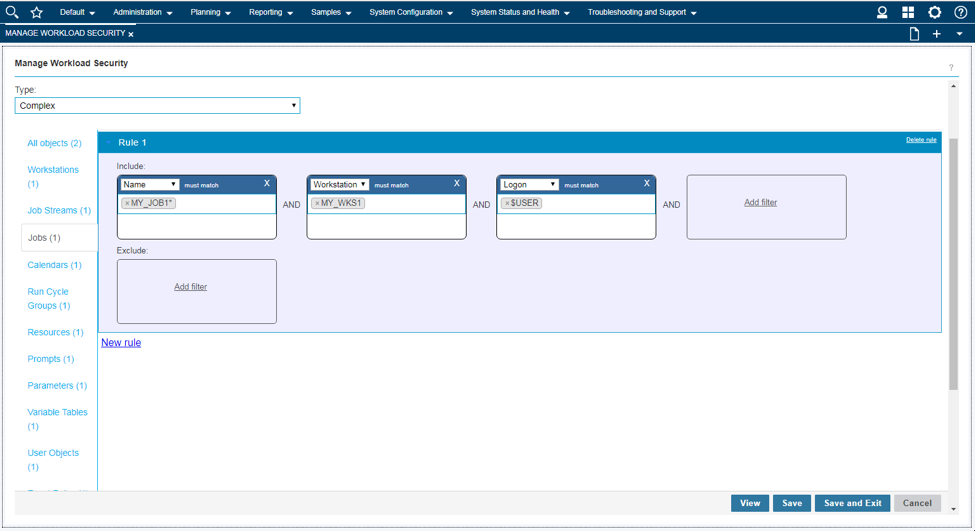
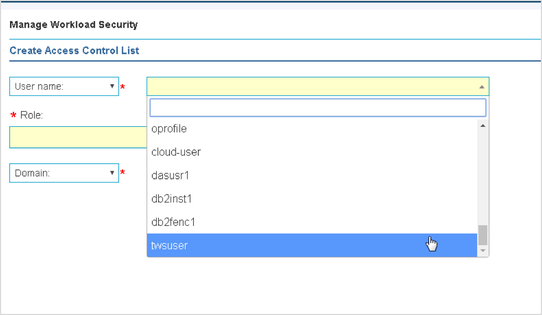
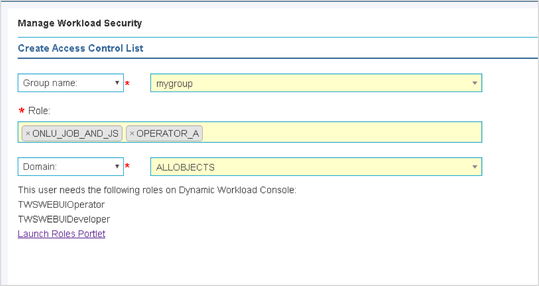
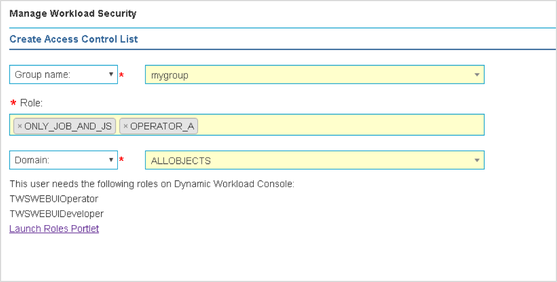
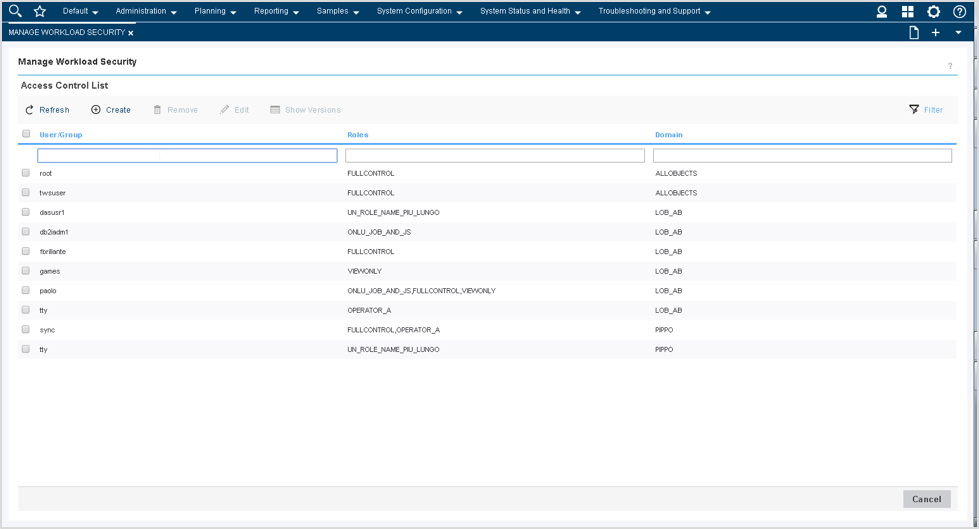
Among the latest enhancements of Workload Scheduler product (also known as TWS – Tivoli Workload Scheduler) there is the new role-based security model to grant and revoke accesses and permissions to Workload Scheduler users. Available from both Command Line Interface (composer) and web interface (Dynamic Workload Console) the new security model introduces some new concepts that simplifies the usage of the Security File. In this post we will see how define accesses from the web console. Manage Workload Security Page This is the entry point to manage the security of Workload Scheduler. Here, you can access different functionalities in one-click (e.g. view access permission for a certain user or group!) Per the new security model, new objects that you can define from the Manage Workload Security page of the web console are: Security Role Each role is a set of actions that user or groups can do on Workload Scheduler objects. Permissions are organized in meaningful sections with predefined subsets: pick yours with just one-click if they fit your needs! For example, the section Manage Event Rules provide No Access, Read-Only, Full Access (with predefined set of permissions) and Custom mode (where you can customize each single action). For each permission there is an association with the security file keywords and a detailed explanation of both general section and single permission itself. Security Domain Each domain represents the set of scheduling objects that users or groups can manage. There is available a bunch of filters you can associate to a domain and create your subset of workload that needs to be associated to someone. You can choose two way of using the Security Domain definition: - Simple: just specify a set of rules that will apply on all the scheduling objects of the scheduler. If you are using a general name convention to organize your objects, you can specify a rule as follows: In this way, user that belong to MY_SECURITY_DOMAIN can see only objects that starts with MY_SUBSET (asterisk is used as wildcard) name but that doesn’t belong to workstation WKS01. In fact, property match can be inclusive or exclusive. The Interface shows AND and OR keywords to let you better understand how the filter will be evaluated. Moreover, multiple rules can be specified to create a larger domain (e.g. objects that starts with AA01 and BB01) - Complex: you can specify permission in the same way but for each Workload Scheduler object Using the “complex” mode, not only Name and Workstation filters can be specified, but for each object you will find a different set of rules that you can specify. Access Control List Each access control list is defined assigning roles to users or groups, on a certain security domain. For users and groups, if available, all the users configured to work with Workload Scheduler are automatically showed in a filterable list. You can also specify a user/group that is not in the picklist of available names. As soon you associate a user/group with a set of roles on a specific domain, the user interface automatically suggest you a set of roles you can associate to a Dynamic Workload Console user that will leverage this ACL. If you are working with LDAP, a good way to customize your ACL is to use groups to simplify security definition. Each of these new objects can be fully managed from a single point of control (the initial page showed at the beginning of this post). Clicking on Manage Access Control List a table with the full list of ACLs is shown. From here you can edit, delete, create objects and see previous versions of the objects.
Francesco is a Software Engineer and Scrum Master experienced in full-stack web development and design. He has worked in the Workload Automation area since 2013 and is currently based in the HCL Products and Platforms Rome software development laboratory. He comes from southern Italy and is a pizza expert, rock music lover, JavaScript geek and SSC Napoli supporter!
7 Comments
12/1/2017 08:40:31 am
Owners of businesses need to know who comes in and out of the building. This kind of knowledge is important for reasons including security and safety. The problem, however, is that tracking every single person who enters and exits the building would be difficult, and hiring a security company to monitor the building can be expensive.
Reply
12/1/2017 08:41:24 am
Owners of businesses need to know who comes in and out of the building. This kind of knowledge is important for reasons including security and safety. The problem, however, is that tracking every single person who enters and exits the building would be difficult, and hiring a security company to monitor the building can be expensive.
Reply
3/26/2018 10:08:12 am
This is a great inspiring article.I am pretty much pleased with your good work.You put really very helpful information. Keep it up. Keep blogging. Looking to reading your next post.
Reply
7/24/2018 10:54:55 am
Locksmiths come in handy when you have locked yourself out of your home and you can't get back in or when for different reasons you have lost your keys. The lock cylinders in a home might also need rekeying at some point or you might have the need to change the locks around your home. They are all services that can be offered by residential locksmiths in and around your place of residence. Locksmith companies specialize in home security systems and high security upgrades.
Reply
9/8/2018 07:34:36 am
Almost always, security guard rates are determined on an hourly basis. Large cities generally cost more for guard service.
Reply
7/12/2019 01:17:03 am
All workmanship and products are guaranteed and we pride ourselves on offering outstanding value for money,
Reply
4/4/2020 02:49:58 pm
Thanks for the blog post buddy! Keep them coming...
Reply
Your comment will be posted after it is approved.
Leave a Reply. |
Archives
July 2024
Categories
All
|


 RSS Feed
RSS Feed